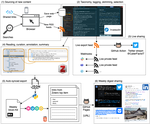
Scalable, Hand-curated Newsletters: A Data-centric, Automatic Workflow
Masked Emotions
Despite this little beast known as COVID-19 pandemic is about to turn 1 year old, many people still feel strange when wearing masks. While wearing a face mask we can’t speak properly and we can’t see others’ mouth, so our experience of a conversation can change, especially if speaking is central in our lives (think of any public figure). Wearing a face mask impacts how we perceive others’ emotions as well as our emotions (how we feel). Because our own understanding of our emotions can also influence such emotions in a continuous feedback loop, the effect can go beyond how we feel in that particular moment.
Reading Aloud
Reading long texts has always been a daunting task to me. A rocky mountain I seldom find myself brave enough to start climbing (unless forced to). I’ve never had good reading habits, except for a few, very intriguing novels with a powerful storyline, which I could actually read quite fast. But most of the readings I wish I could get done quickly are damn hard. In the era of book-summarizing services like Blinkist, audiobooks, and “CEO reading guides,” where people invest time and money to compress time and read more, my limited reading abilities are an actual obstacle to my knowledge development. How did I change that? I don’t know if I did, but here is what I found by experimenting on myself.
Smart Manufacturing Security
How do we secure a smart manufacturing system, or a smart factory? Recent incidents such as the ransomware infection that halted production at a major semiconductor foundry in 2018 have already shown the impact of IT-to-OT lateral movement. Moreover, while smart manufacturing systems are isolated from other networks, there is a trend toward less isolation between IT and OT systems.
Radio Killed the Radio Stars: Security Analysis of RF Protocols for Industrial Applications
After having analyzed the several RF protocols for industrial applications, distributed by global vendors, we discovered that none of them had sufficient security features to prevent an attacker from hijacking the communication and manoeuvre the controlled connected machines.
Large Scale Analysis of Defaced Web Pages
Given the multiple releases around this topic and project, I’ve decided to put together a summary. So far, there is: a tool, a white paper, an academic paper, and (spoiler alert) another white paper coming soon.
Dnsmasq and CVE-2017-1449*: A Reality Check and Remediation Practices
Many vulnerabilities in one shot, yet several pre-conditions for a target to be actually exploitable. Here’s simple flowchart to check whether your Dnsmasq deployments are vulnerable.
Robosec: Industrial Robot Security
Industrial robots are complex cyber-physical systems used for manufacturing, and a critical component of any modern factory. Besides the mechanical arm, inside an industrial robot there are not just electromechanical components but a multitude of complex embedded controllers.
From a Bit-flipping to a Vulnerability in the CAN Standard
CAN-based protocols are vulnerable to bit-flipping attacks at the link layer. In this collaborative research, Politecnico di Milano’s NECSTLab and Trend Micro’s FTR analyze the protocol in depth and demonstrate the vulnerability on a real car, with PoC and so on.
Prometheus: Automatic signature generation for WebInject-based banking trojan detection
The goal of this project is to extract signatures that capture the WebInject behavior of trojans. WebInject-based trojans are still the most popular e-crime tool.