🔓 [CyberFacts Weekly - Issue 0x01] A Packed Week
Malware targeting gamers / VSCode extension with command injection / OWASP turns 20 / Chrome fixes an RCE / AirTags can carry XSS payload / PoC exploit for VMware CVE-2021-22005 / More Apple bug bounty drama / Android bankers / Bitcoin ATMs vulnerable to tampering / New SolarWinds details / When ransomware hits hospitals / Bug in ApplePay Express Mode with VISA / Threat actors posing as Amnesty

Hello ☺️
The second issue of CyberFacts Weekly is out and I have to say that I’m quite happy to see a (slowly) growing interest around both this weekly digest and the live feed (available via Twitter and RSS).
It’s been quite a packed week: It wasn’t easy to keep track of all the interesting events. Also, I decided to open each weekly issue with the image Tweeted by the @archillect AI at the time of writing.
Towards the end of this digest, I took some room for a reflection about the current state of conferences, and what I foresee for their future.
Note: I deliberately avoided to include in this issue the new developments regarding Group-IB and Julian Assange; despite the latter case is certainly shocking, I strive to keep this feed and digest free from stories that are highly connected with political and geo-political matters, and focus only on the technically relevant events.
Enjoy!
-
This Week’s Top Picks
- #gaming | Malware specialized in stealing gamers’ assets
- #coding | VSCode Remote Development extension had a now-fixed command-injection vulnerability
- #iot | 2 cticial vulnerabilities fixed in QNAP video-surveillance NAS solution
- #appsec | OWASP turned 20 and XSS is now bundled into ‘injection attacks’ in their Top 10
- #vuln | Google fixes critical RCE vulnerability in Chrome (CVE-2021-37973)
- #apple | Apple vs. Bug Bounty: Take II - Fed-up researcher speaks louder
- #cloud | Public exploit available for VMware vCenter CVE-2021-22005
- #mobile | AirTag Lost Mode API allowed JavaScript injection enabling client-side redirection attack
- #mobile | GriftHorse Android trojan steals millions by subscribing to paid $35/mo services
- #supplychain | Updated timeline adds new details to the SolarWind incident
- #cloud | Azure AD is still vulnerable to “by design” flaw that allows single-factor brute-force attacks
- #bitcoin | US Bitcoin ATMs, which run on COTS Linux-based embedded platforms, has been found to have interesting vulnerabilities and no tamper-proof design
- #crypto | Bug in Apple Pay with VISA allows above-the limit transactions via man-in-the-middle even when the iPhone is locked at rest
- #web | Let’s Encrypt’s Root CA Certificate is expiring, and we’re getting a new one good ’til 2024
- #macmalware | Mac users targeted (again) by trojanized iTerm2 app
- #ransomware | When ransomware hits a hospital with no backup plans, who’s responsible of the consequences?
- #malware | Threat actors posing as Amnesty International exploit the fear of Pegasus to spread malware
-
Also Noteworthy
- #fraud | FBI arrests business email compromise (BEC) scammers which stole around $17 million
- #privacy | Fastmail now selling masked email-alias integration with 1Password
- #mobile | ERMAC, a new Androind banking trojan derived from Cerberus rented for $3k/mo
- #windows | Windows low-level substrate (WPBT) can be leveraged to write rootkits
- #surveillance | FinSpy/FinFisher now discovered to have a multi-staged, modular UEFI module: A “piece of art”
- #vulns | Timeline of high-impact vulnerabilities since 2019
- #malware | Zeus nostalgia: Zloader infographics since 2019
- #blockchain | Tracking Monero WannaCry 2.0 transactions thanks to an open, now fixed, ShapeShift API
- #mobile | Android banking trojan steals instant-payment Pix currency
- #acquisition | Akamai acquires Guardicore
- #ecrime | Criminals are interested in stealing OTP tokens via Telegram bots
- #nft | Scammers on Discord posing as OpenSea Support Operators scammed collectors and stole hundreds of thousands of dollars worth of NFT
- #crypto | Stealing crypto keys from phones via EM side channels
- Tools
- Conferences
This Week’s Top Picks
#gaming | Malware specialized in stealing gamers’ assets
by Kaspersky
As professional gamers become valuable individuals, cybercriminals are increasingly showing interest in stealing their assets, which include their account credentials to access popular gaming platforms such as Steam and Origin.
Kaspersky researchers have found evidence of cybercriminal actors advertising and selling a malware dubbed “BloodyStealer”, specialized in stealing gaming assets.
#coding | VSCode Remote Development extension had a now-fixed command-injection vulnerability
by Shielder
Extensions are always the weak link of a well-developed and well-secured software. I guess everyone remembers how many times vulnerable WordPress extensions have become the door opener to popular websites.
Development environments such as VSCode are no exceptions. At the end of the day, extensions are just “more code” in the game. The Italian Shielder has discovered that a remote-development extension, making heavy use of SSH as a secure transport, was vulnerable to comand injection.
#iot | 2 cticial vulnerabilities fixed in QNAP video-surveillance NAS solution
by Ionut Ilascu for Bleeping Computer
QNAP has just fixed two critical vulnerabilities (CVE-2021-34351 and CVE-2021-34348) in their video surveillance solution, which could be exploited to run arbitrary commands. Needless to say, NAS endpoints have become a very juicy target, exposing consumers to more enterprise-like threats, because of the data and computation resources offered by modern NAS boxes.
#appsec | OWASP turned 20 and XSS is now bundled into ‘injection attacks’ in their Top 10
by Jessica Haworth for The Daily Swig
Happy 20th birthday OWASP! 🎂 What better way to celebrate than publishing a revised Top 10 list! In the updated list, injection attacks are now the 3rd most popular attack (were number one) and, most importantly, XSS is not a standalone bug class anymore: It’s now part of the broader “injection” class. Broken access control is now the most serious web application risk.
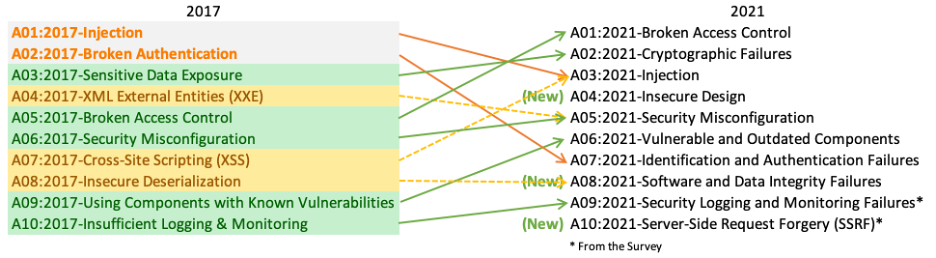 (Source:
https://owasp.org/Top10/)
(Source:
https://owasp.org/Top10/)
#vuln | Google fixes critical RCE vulnerability in Chrome (CVE-2021-37973)
by US-CERT and Google
Google has just released quite an important patch to address CVE-2021-37973, which could be exploited to take control of a vulnerable system. Also, an exploit for this vulnerability exists in the wild! So, make sure your on the latest Chrome version: 94.0.4606.61.
#apple | Apple vs. Bug Bounty: Take II - Fed-up researcher speaks louder
by Denis Tokarev
Another week, another drama. Well, it’s not just drama: It’s serious business! Running a bug bounty program is quite hard, but it seems that Apple could really use some help. After dropping 3 0-days last week, fed-up researcher Denis Tokarev, which findings have not received the deserved attention, is back with a louder voice. This time he’s explaning (also through the neat narration of Motherboard’s Lorenzo Franceschi-Bicchierai) how Apple should do better, and how App Store’s static analysis checks, which are supposed to prevent malware from crippling in, can be bypassed.
#cloud | Public exploit available for VMware vCenter CVE-2021-22005
by Ionut Ilascu for Bleeping Computer
Within a week we went from knowing about actors scanning for VMware targets vulnerable to CVE-2021-22005 to having a publicly available exploit PoC. On the good side, if your signatures aren’t yet up to date, the availability of a public PoC will certainly help refining them.
#mobile | AirTag Lost Mode API allowed JavaScript injection enabling client-side redirection attack
by Bobby Rauch
This is quite a neat attack PoC, despite leverging “just” an injection bug. I like it because it involves a physical device that, essentially, “carries” the injection exploit.
“I can’t remember another instance where these sort of small consumer-grade tracking devices at a low cost like this could be weaponized,” Rauch said.
(source: Brian Krebs)
The vulnerability per sé is nothing really sophisticated, because it’s a parsing bug that does not prevent an attacker to inject client-side JavaScript code instead of the phone number, but the exploitation and the effect is quite theatrical.
You (attacker) set an AirTag in lost mode, inject a short line of JavaScript that redirects to a (malicious) website that you control, instead of the phone number. The victim scans the tag with the phone and, instead of being “redirected” to the phone number (which is the expected, by-design behavior), they’ll get automatically redirected to the malicious website.
Want more drama? Here we go:
Rauch [the researcher who found the bug] said he’s reported many software vulnerabilities to other vendors over the years, and that Apple’s lack of communication prompted him to go public with his findings — even though Apple says staying quiet about a bug until it is fixed is how researchers qualify for recognition in security advisories.
(source: Brian Krebs)
#mobile | GriftHorse Android trojan steals millions by subscribing to paid $35/mo services
by Zimperium zLabs
If you thought that “dialer” malware is a thing from the past, GriftHorse is the modern take on good ol’ dialers.
Dialers are software that change modem configurations to dial high cost toll numbers or request payment for access to specific content.
Instead of dialing premium numbers, GriftHorse surreptitiously subscribes your phone to premium services that can cost up to $35/month. This way, the actors behind GriftHorse have managed to make hundreds of millions of Euros by infecting up to 10 million victims globally, according to the research.
#supplychain | Updated timeline adds new details to the SolarWind incident
by Kasperksy
Kaspersky’s GReAT team has unveiled some more details connected to the SolarWinds incident, including a previously-unknown malware family dubbed Tomiris, which shares several similarities with the Sunshuttle second-stage malware (both written in Go, packed with UPX, same configuration syntax, same C2 traffic encryption, etc.), found and analyzed by FireEye and Microsoft when investigating the SolarWinds incident.
#cloud | Azure AD is still vulnerable to “by design” flaw that allows single-factor brute-force attacks
by Dell Secure Works
Secureworks® Counter Threat Unit™ (CTU) researchers found a flaw in the protocol used by Azure Active Directory Seamless Single Sign-On feature, that would allow an attacker to stealthily brute-force sign-in attempts, without leaving any traces. After responsible disclosure to Microsoft, the flaw was confirmed, but won’t be fixed because considered a “by-design” behavior.
#bitcoin | US Bitcoin ATMs, which run on COTS Linux-based embedded platforms, has been found to have interesting vulnerabilities and no tamper-proof design
by Kraken Security Labs
Behind an ATM there’s a computer, and that’s no surprise. Bitcoin ATMs are no exception. The researchers of the Kraken Security Labs have performed a full-blown pen-test of a Bitcoin ATM popular in the US and have found out that:
a large number of ATMs are configured with the same default admin QR code, allowing anyone with this QR code to walk up to an ATM and compromise it.
In addition, they found out that the single-board computer used to power these devices is used “as is,” without any tamper-proof additions, which are usually necessary in these applications to record any traces of tampering attemps (e.g., the cabinet should have a sensor that logs every attempt of opening, and possibly put the device in some sort of “open mode”).
Although we shouldn’t forget about the threat model (i.e., it’s suspicious to see anyone tampering with an ATM), it seems that these devices are not hardened enough to make it difficult for an attacker to open the cabinet and plug-in a USB key.
#crypto | Bug in Apple Pay with VISA allows above-the limit transactions via man-in-the-middle even when the iPhone is locked at rest
by Ionut Ilascu for Bleeping Computer
Apple Pay, when used with VISA and Express Mode, exhibits a bug that can be leveraged to raise the transaction limit, from a locked iPhone (e.g., in your pocket).
The original paper has been presented at the 6th IEEE European Symposium on Security and Privacy (EuroS&P).
#web | Let’s Encrypt’s Root CA Certificate is expiring, and we’re getting a new one good ’til 2024
by Scott Helme
One thing that I do know, though, is that at least something, somewhere is going to break.
And it did happen:
Helme told ZDNet that he confirmed issues with Palo Alto, Bluecoat, Cisco Umbrella, Catchpoint, Guardian Firewall, Monday.com, PFsense, Google Cloud Monitoring, Azure Application Gateway, OVH, Auth0, Shopify, Xero, QuickBooks, Fortinet, Heroku, Rocket League, InstaPage, Ledger, Netlify and Cloudflare Pages
While The Register has reported about Xero and Slack outages, but the “Internet” is still working.
#macmalware | Mac users targeted (again) by trojanized iTerm2 app
by Trend Micro
There’s a Python-based malware targeting Mac users, packaged into fake, trojanized iTerm2 app being advertised in Q&A forums. The malware collects private data. This research is a follow-up to Objective-See’s previous analysis on the same family.
#ransomware | When ransomware hits a hospital with no backup plans, who’s responsible of the consequences?
by Threatpost (and WSJ)
Mixed feelings about this one.
— Federico Maggi (@phretor) September 30, 2021
This is *alleged* malware-related death #2 in my list, after the ambulance which was rerouted to another hospital because of a ransomware-induced downtime.
The problem lies in too much reliance on IT in critical situations and no backup plans. https://t.co/6vktKTrX7n
I think there is a case of an ambulance (which would make this #3), but I could not find it. However, I found this case occurred back in 2020.
For the first time ever, a patient’s death has been linked directly to a cyberattack. Police have launched a “negligent homicide” investigation after ransomware disrupted emergency care at Düsseldorf University Hospital in Germany.
But it’s not really important if it’s the third, second, or first case. I see things differently, and I don’t think we should fingerpoint to the ransomware:
So, no, it's not the first ransomware-linked death.
— Federico Maggi (@phretor) September 30, 2021
And of course I'm among those who think that ransomware is the root cause.
If a life-critical service is relying on tech without a back up plan...the poor security/threat model is the cause. https://t.co/o5X34X5LK8
#malware | Threat actors posing as Amnesty International exploit the fear of Pegasus to spread malware
by Cisco Talos
Just a few weeks since Amnesty International has published their detailed forensics analysis of the Pegasus spyware kit, Cisto Talos researchers have found an actor leveraging the fear around Pegasus, posing as Amnesty Internation to fool victims into installing the little-known Sarwent malware. A wolf in sheep’s clothing, as the title of the blog post says.
Also Noteworthy
#fraud | FBI arrests business email compromise (BEC) scammers which stole around $17 million
by Catalin Cimpanu
US officials said the group had been active since at least January 2017 and engaged in a wide range of fraudulent schemes, such as business email compromise (BEC), investor scams, and unemployment insurance fraud.
#privacy | Fastmail now selling masked email-alias integration with 1Password
by Fastmail
If you’re a Fastmail user, great, you can enable this integration to have privacy-preserving email aliases that can masquerade your true, email address. If you’re not, Fastmail will offer you a discount on the first year of subscription.
I’m a 1Password user and I think this functionality makes a lot of sense (*), but it’s hard for me (as it is to anyone, I guess) to change email provider.
(*) In my view, each time you subscribe to a website, email alias and password should be automatically and transparently generated at random by a kernel-backed password manager with secrets managed in a hardware-supported trust zone, without any user interaction. I’m still waiting for a standard API that supports all of these operations. Websites should get APIs for registration and password changing operations, while kernels should get a uniform API to set-get secrets using a least-privilege model (i.e., unlock only the secret pertaining to the website in question).
#mobile | ERMAC, a new Androind banking trojan derived from Cerberus rented for $3k/mo
by Threat Fabric (and THN)
ERMAC is almost fully based on the well-known banking trojan Cerberus, and is being operated by BlackRock actor(s).
and it’s advertised, as a service, in undergound forums:
“Android botnet ERMAC. I will rent a new android botnet with wide functionality to a narrow circle of people (10 people). 3k$ per month. Details in PM.”
#windows | Windows low-level substrate (WPBT) can be leveraged to write rootkits
by Eclypsium
Every modern computer has the ACPI (introduced in the early 2000s). Every Windows installation since Windows 8 has WPBT. So what? Well, these two make an explosive cocktail, making it the perfect place for a rootkit!
I’m going to quote Dino Dai Zovi’s here:
Yet another example of the fine folks at @eclypsium dropping The K-nowledge:https://t.co/uwgjwFE10b
— Dino A. Dai Zovi (@dinodaizovi) September 28, 2021
#surveillance | FinSpy/FinFisher now discovered to have a multi-staged, modular UEFI module: A “piece of art”
by Kaspersky
we found out that the backdoored installers are nothing more than first stage implants that are used to download and deploy further payloads before the actual FinSpy Trojan.
Apart from the Trojanized installers, we also observed infections involving usage of a UEFI or MBR bootkit. While the MBR infection has been known since at least 2014, details on the UEFI bootkit are publicly revealed in this article for the first time.
It is also multi-staged, modular, is capable of parasitic binary infection and contains polymorphic properties. It is a piece of art.
— vx-underground (@vxunderground) September 28, 2021
#vulns | Timeline of high-impact vulnerabilities since 2019
by Paolo Passeri
I wasn’t aware of the work patiently put together by Paolo Passeri, but he makes pretty nice timelines! In this one, he’s selected the most impactful (according to his technical judgment) vulnerabilities since 2019.
#malware | Zeus nostalgia: Zloader infographics since 2019
by Trend Micro
Remember Zeus? I’ve used it in so many training when I was teaching malware analysis at the university. Have a look at this infographics by Trend Micro, about Zloader, one of the active Zeus variants.
#blockchain | Tracking Monero WannaCry 2.0 transactions thanks to an open, now fixed, ShapeShift API
by Nick Bax
According to leaked slides:
Monero transactions related to the WannaCry 2.0 ransomware were traced as they were converted back to the transparent BTC and BCH blockchains. Here, I demonstrate how the WannaCry 2.0 funds were traceable using publicly-available information.
#mobile | Android banking trojan steals instant-payment Pix currency
by Check Point
These malicious apps, once distributed on Google Store, seem to be an evolution of an unclassified family of Brazilian bankers […]
It’s the week of Android currency stealers, isn’t it?
#acquisition | Akamai acquires Guardicore
by Guardicore
#ecrime | Criminals are interested in stealing OTP tokens via Telegram bots
by Intel471
Intel 471 has seen an uptick in services on the cybercrime underground that allow attackers to intercept one-time password (OTP) tokens.
[they] either operate via a Telegram bot or provide support for customers via a Telegram channel. In these support channels, users often share their success while using the bot, often walking away with thousands of dollars from victim accounts.
#nft | Scammers on Discord posing as OpenSea Support Operators scammed collectors and stole hundreds of thousands of dollars worth of NFT
by Andrew Wang for The Verge
I’m a little late on this one, but I wanted to keep track of it. I want to keep an eye on this topic, because I think we’re going to see a lot of these scams.
#crypto | Stealing crypto keys from phones via EM side channels
by Georgia Tech
Catching EM emissions produced by a computer to infer the data manipulated by a CPU during crypto operations isn’t a new technique: It’s called TEMPEST attack. But seeing this practically applied to a real, mainstream phone in non-lab conditions is a step forward! How many times have you checked below the surface before placing your phone on it?
Tools
Facebook open-sources static analysis tool to find bugs in Android and Java apps
by Facebook
Can’t wait to test it on a recent app. Maybe a COVID19 vaccine-pass checkers? 😇
Conferences
Security Analyst Summit (SAS) 2021
by Kasperksy
This year’s SAS has really set the new bar of virtual conferences:

(source: Threatpost)
I literally fell in love with how the organizers have prepped the speakers and turned them into actors, basically. Including remote speakers! I guess each speaker went through some short training, they got shipped clothes, etc., and the idea of connecting them in the studio by bringing in a Trinitron TV set just blew my mind when I saw it. Not to mention the backstage with the telephone-switch-like atmosphere, typewriters, people playing chess. Amazing, absolutely amazing. 👏 Of course, this takes a hell of logistics and organization work behind the scenes.
Conference organizers: please take inspiration!
Eye-candy-look aside, allow me a short reflection about conferences in the post-COVID era. I think we all got the point: talks alone are a bit pointless. Pre-recorded talks especially are very easy to recycle, that they loose completely the “exclusivity” that justifies a 15-hours flight to attend them. To be completely honest, I don’t kwnow about other sectors, but cybersecurity folks travel to conferences primarily for the so-called “corridor con,” which IMHO is the best of all the tracks as it lets you connect with colleagues and peers around the world.
A lot of the responses to this tweet have been about the social/networking aspect of conferences. Okay, if that’s the value of conferences, let’s start having conferences without talks. https://t.co/4OR5cyOsL6
— Charlie Miller (@0xcharlie) September 5, 2021
So, how do we make talks attractive again? We should make them fun, entertaining, theatrical. What about pre-recording? Yes, why not, we can still do pre-recording, but we shold move away from the “cheap-looking” pre-recorded talks if we want people to watch them. I foresee bigger conferences getting more and more specialized in producing high-quality, exclusive videos. Like Netflix? Not yet, but that’s the spirit. You want people to attend a (virtual) conference because of exclusive, eye-candy and well-produced content, in the same way you want people to attend a physical conference to get together with peers and be entertained.
Black Hat Europe 2021 full briefings lineup announced
Shameless plug: I’ll be speaking about the security of a not-so-popular but extremely ubiquitous critical protocol called DDS. Check it out, and please stop by if you’ll attend the conference!
RomHack 2021 Recordings Published
Slides and full recordings of the Italian RomHack 2021 are available!
IEEE Euro S&P 2021
I’m a little late on this one, but the list could not be complete without EuroS&P!
CyberFacts Weekly is a digest of my hand-picked readings from the cyber-security world.
CyberFacts Weekly is intended mostly for myself, to have a place to archive and keep public notes of what I read and deem as noteworthy.
If you like it, consider subscribing or forwarding this email to peers and friends. If newsletters aren’t really your thing, maybe you’d prefer to follow the @CyberFactsIT Twitter account, which I use to publish the real-time feed of my selected readings (also available via RSS).
Hope you enjoyed this issue…and see you reading the next one! 🙃
Thanks! Cheers, Fede